-
Introducing AI Security Code Review
Traditional AppSec misses critical design flaws? Discover Endor Labs' AI Security Code Review, a revolutionary agentic AI platform that analyzes pull requests for hidden architectural changes, new API endpoints, and authentication logic modifications, ensuring you catch high-impact security risks that rule-based tools miss.
-
Meet the application security platform built for the AI era
The era of vibe coding is here. Learn how Endor Labs is helping AppSec teams secure and fix AI-generated code with a new agentic AI platform.
-
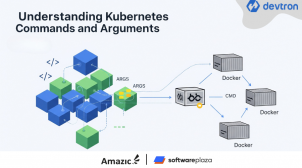
Understanding Kubernetes Commands and Arguments
Want to customize what runs inside your Kubernetes containers? This blog shows you how to use commands and arguments to override Docker defaults, with practical examples and use cases like running startup scripts and testing network connectivity.
-
Driving Beyond Visibility: Why Action Is the True Currency of FinOps
In the 2025 State of FinOps report, workload optimization and waste reduction once again top the list of priorities—but this time, it's about action, not just visibility. As FinOps matures, the focus is shifting from simply identifying inefficiencies to systematically fixing them through built-in workflows, context-rich insights, and tighter engineering integration. This article explores how governance, automation, and cultural alignment are shaping the next frontier of FinOps—where every dollar saved is tracked, verified, and sustained at scale.
-
ASPM is for Everyone
ASPM isn't just for security teams anymore! Discover why developers are the new frontline in AppSec and how Checkmarx is bringing powerful Application Security Posture Management (ASPM) directly into their IDEs, unifying insights and focusing on exploitable risks for friction-free, AI-powered security.
-
API Security Testing: What it is, Why it Matters
APIs power modern applications but also expose critical vulnerabilities that attackers often exploit. This article explores why API security testing is essential, how breaches like MOVEit happened, and what organizations can do to protect their APIs. It also highlights the differences between REST, SOAP, and GraphQL security, and how tools like OX Security help ensure complete visibility and protection across the API landscape.
-
OX Security: Empowering Executives with Actionable AppSec Insights
Application security isn’t just a technical concern — it’s a business priority. OX Security’s enhanced executive reports help bridge the gap between AppSec teams and leadership by turning complex security data into clear, actionable business insights. With high-level summaries, dynamic visualizations, and tailored risk analysis, these reports empower executives to prioritize security investments and align AppSec strategies with business goals.
-
The use of AI has become the expectation, Are you keeping up?
Is AI truly reflexive in your company? Discover why saying "no" to AI multiplies risk and how secure, owned AI solutions like Civo's relaxAI can boost productivity, improve decision quality, and transform your organizational culture, ensuring your teams harness AI without sacrificing control or compliance.
-
Is AI already replacing me? Insights from Civo Navigate
Are you keeping up with AI's rapid evolution? Dive into key takeaways from Civo Navigate, exploring multimodal AI, agentic systems, and anomaly detection. Discover how AI is augmenting, not replacing, humans, the impact of open-source models, and the crucial debate on responsible AI adoption.
-
From Alerts to Actions: Turning AppSec Data into Business Value
Modern AppSec teams are overwhelmed with alerts but still struggle to answer the one question that matters: What should we fix first? This article explores how shifting from raw data to contextual insights helps prioritize the most impactful vulnerabilities, align security efforts with business goals, and move application security from a cost center to a strategic enabler.
-
Understanding SBOM Software: The Foundation of Modern Cybersecurity
A Software Bill of Materials (SBOM) is the key to understanding what’s inside your software—and securing it. This article explores the growing importance of SBOMs in cybersecurity, the difference between static and dynamic SBOMs, how AI is transforming their effectiveness, and best practices for managing software supply chain risk.
-
A Costly Divide: 5 Ways to Stop AppSec and Dev from Working Against Each Other
The disconnect between AppSec and development teams is more than a collaboration issue—it’s a major business risk. This article explores the root causes of this divide, from misaligned goals to disconnected toolchains, and offers practical strategies for uniting teams. Learn how to embed security into the developer workflow, prioritize risk over noise, and foster a culture of shared responsibility and continuous improvement.
Filter & Sort