-
How much does pen testing cost? [2025]
Explore the true costs of penetration testing in 2025, breaking down pricing by scope (web, mobile, API, cloud, network, IoT) and methodology (black box, grey box, white box). Discover key factors influencing costs and learn how AI-powered solutions like Beagle Security offer a faster, more affordable alternative to traditional pen tests.
-
Diskless Kafka is the Tide, and it’s Rising
Discover KIP-1150 Diskless Topics now live in Aiven Kafka BYOC, enabling Apache Kafka on AWS, Google Cloud, and Azure to write directly to object storage. Learn how this innovation slashes costs by up to 80%, eliminates operational toil, and maintains 100% Apache Kafka compatibility, ensuring zero vendor lock-in and a single logical cluster for all streaming workloads.
-
PostgreSQL® extensions you need to know in 2025
Uncover the pivotal role of PostgreSQL's extensions ecosystem, its historical context, and why it remains indispensable for modern data needs, including AI and analytics. Dive into key extensions like TimescaleDB, PostGIS, and pgvector, and learn how a managed service, like Aiven, mitigates risks and enhances reliability.
-
The 3 Es of Diskless Kafka BYOC
Explore three ways to buy Kafka in the cloud—Multi-Tenant SaaS, Single-Tenant SaaS, and Bring Your Own Cloud (BYOC)—and discover why Diskless BYOC offers significant economic, enforcement, and enterprise discount advantages for organizations operating Kafka at scale, challenging traditional fully-managed solutions.
-
Optimizing K8s Cost to Strengthen Competitive Advantage
Discover how cybersecurity leader Cynet, with a focus on simplicity, leveraged PerfectScale to gain unprecedented visibility into pod costs, streamline Kubernetes cost optimization, and proactively identify and resolve resiliency issues across their multi-cluster AWS EKS environment, ensuring a stable and cost-effective solution for their customers.
-
How Rapyd Solved Observability Gaps to Cut K8s Costs by 40%
Discover how fintech leader Rapyd partnered with PerfectScale to close observability gaps in their Kubernetes environment, achieving a projected 35-40% reduction in K8s costs while simultaneously improving performance and proactively resolving critical issues across their extensive AWS EKS infrastructure.
-
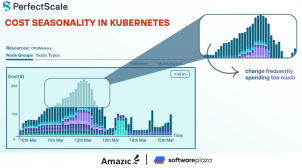
Understanding Cost Seasonality in Kubernetes
Unpack the concept of cost seasonality in Kubernetes, explore the factors that drive its fluctuations, and discover effective strategies—including right-sizing, autoscaling optimization, and leveraging tools like PerfectScale—to manage and predict your cloud spend while maintaining performance.
-
FinOps in 2025: The 6 Phases of FinOps Evolution
Explore the six evolving phases of FinOps, from the initial "Observational" data collection to "Automated" and the future of "Integrated FinOps," revealing how organizations learn to manage cloud spend and optimize infrastructure efficiently over time.
-
Kubernetes Cost Optimization: From Roadblocks to Results
Discover how Trax, a leader in retail technology, leveraged PerfectScale to overcome manual Kubernetes optimization roadblocks, achieving an astounding 75% cost reduction in one cluster (saving over 6-figures annually) and significantly improving their "cost per processing" metric by gaining granular visibility and actionable insights across their multi-cloud, multi-cluster AWS EKS environment.
-
How PerfectScale Helps a DevOps Team of One Scale Riftweaver
Discover how Riftweaver, an innovative gaming studio with a one-person DevOps team, leveraged PerfectScale to reduce CPU throttling by nearly 59% in critical APIs, improve user experience, and enable efficient scaling of their AWS EKS Kubernetes environment, even on a free plan.
-
Meta Launches New Llama 4 AI Models ‘Scout’ and ‘Maverick’ to Power Innovation
Meta launches Llama 4 Scout & Maverick, open-source AI models focused on multimodal capabilities to rival GPT-4 and power next-gen applications.
-
Latest Advancements in Confidential Computing to Improve Data Security
Explore how confidential computing transforms cloud security by protecting data in use, which is crucial for data-sensitive sectors.
Filter & Sort